Author: – INFORMATIKA –
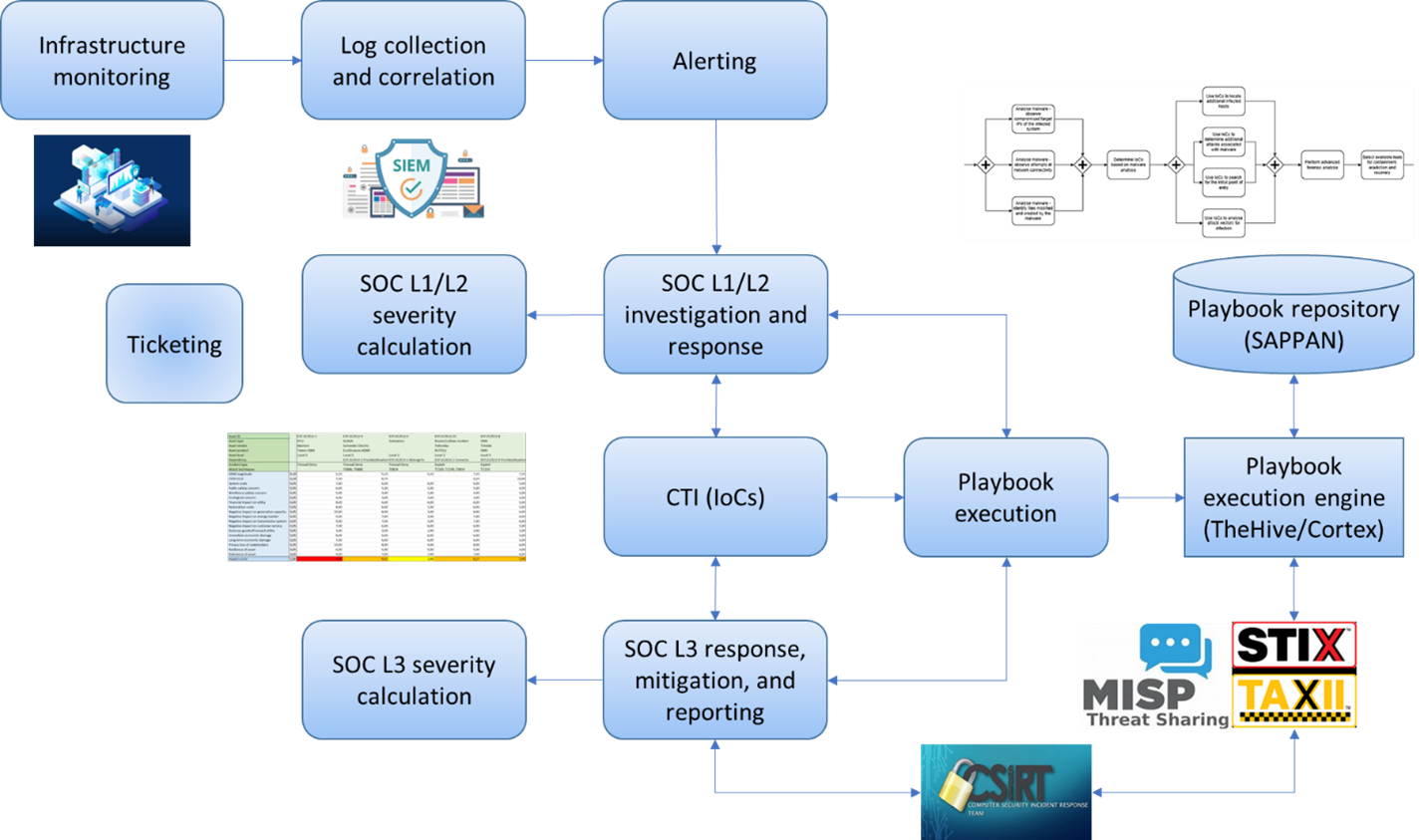
Efficient incident response is fundamental in cybersecurity as it limits the impact of cybersecurity incidents, shortens the recovery time, and reduces the required costs. When applied to the critical EPES infrastructure, it must incorporate the perspectives of different stakeholders participating in common energy supply chains, follow national regulations and rules, and ensure regulatory compliance with the NIS 2 directive to improve the cooperation between EU countries and meet the tightened reporting requirements in case of large-scale incidents, implying that incidents must be reported to national CERTs based on their severity in a prescribed way. To deal with these issues, CyberSEAS introduces a playbook for collaborative activities among SOCs and CERTs in the electricity sector, consisting of incident response procedures and tools that share the status among CERTs to support a coordinated response to incidents and reduce their impact on the critical EPES infrastructure.
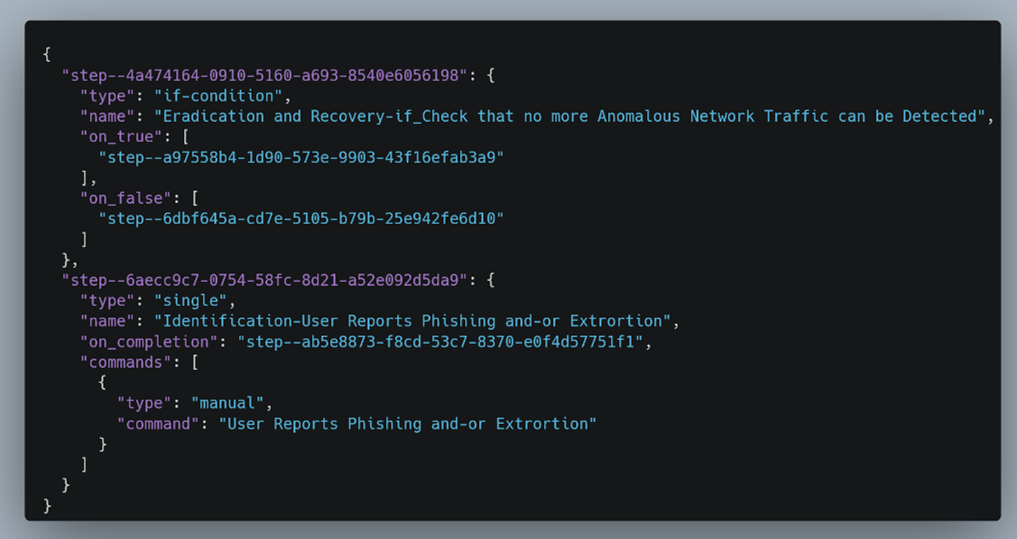
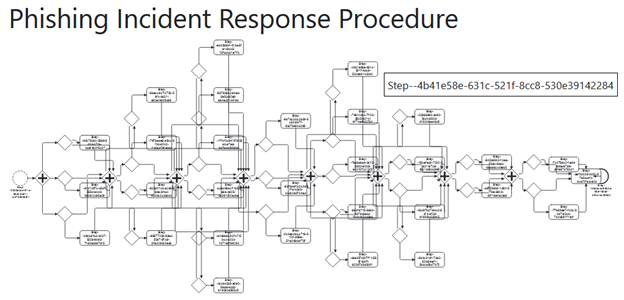
For standardized reporting, it is essential to consider the specifics of legislation in different EU countries. CyberSEAS hence defines national incident response procedures consisting of containment, eradication, recovery, and reporting activities. These procedures are modelled with process diagrams by applying the SAPPAN tool, which also serves as the playbook repository allowing for the exchange of models. The standard BPMN notation is mapped to the lower-level CACAO notation using a common vocabulary. Specified rules determine the required levels of coordination with CERTs, stating when and how incidents are reported to CERTs according to their classification, severity, scope, and functional and informational impact. CyberSEAS also introduces a toolset that facilitates L1, L2, and L3 SOC. It is built upon several tools and technologies, which include SAPPAN for playbook modelling and management, TheHive and Cortex for incident investigation and playbook execution, SIEM for incident detection, and MISP for reporting and collaboration with CERTs.
To establish competent incident response procedures and rules for coordination with CERTs, CyberSEAS performed a comprehensive analysis of national practices, focusing on several aspects that highlight many similarities between different EU countries:
- Required coordination with CERTs: Operators of essential services and digital service providers are obliged to forward notifications of cyber incidents with a significant impact to national CERTs.
- Incident response procedures and rules: They are based on the ISO 27001/27035 IT governance model or the NIST IR process consisting of preparation, detection & analysis, containment, eradication & recovery, reporting, and post-incident activities.
- Data structures, formats, and tools for reports: Standardized incident reporting forms, automated processing of alerts from integrated systems, specific tools for incident reporting (such as the EU’s CSIRT Notification Format), STIX/TAXII, and TLP (Traffic Light Protocol) are applied.
Communication strategy and information-sharing mechanisms: They are based on real-time IR, information sharing, technical support, coordination with other CERTs, and public and situational awareness.