Author: – INFORMATIKA –
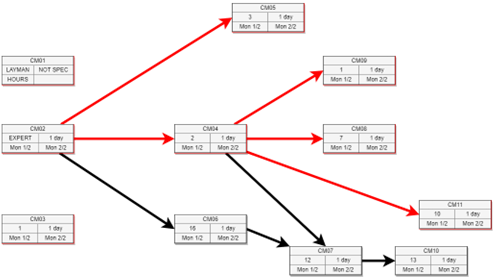
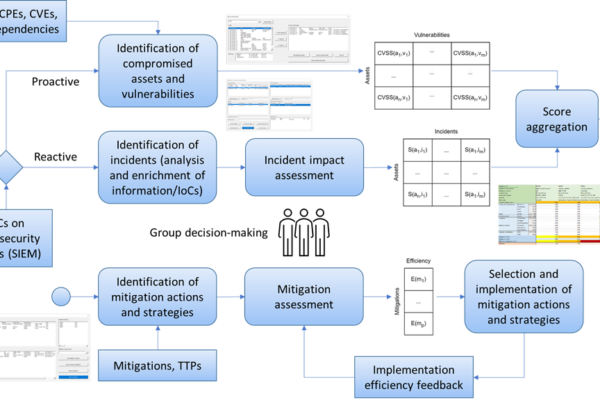
The implementation of suitable mitigation measures against cyber threats and attacks plays a crucial role in elevating the resilience of ecosystems. This is of particular significance in critical infrastructures, such as EPES. However, as mitigation measures encompass both advantages as well as costs, a proper selection of them is essential. CyberSEAS introduces a comprehensive decision-making methodology that helps EPES stakeholders assess, choose, and implement cost-efficient mitigation actions and strategies. A decision support system (DSS) is developed that covers all phases of the multi-criteria decision process. It addresses dependencies between IT/OT assets and facilitates group decision-making on different organizational levels and between different stakeholders participating in energy supply chains, hence reducing the cascading effects of cyber-attacks.
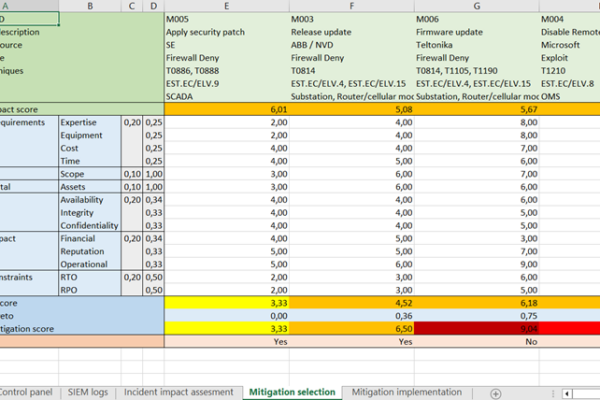
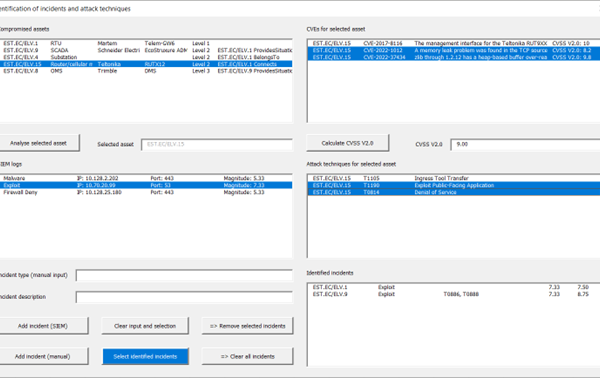
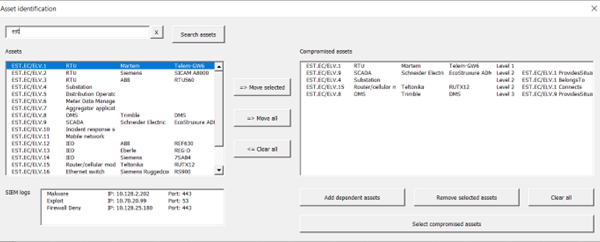
By using the DSS, EPES stakeholders are enabled to identify cyber threats and incidents and evaluate their impacts on compromised assets. The input information can come from the SIEM system following the reactive mitigation approach, or from the risk management system facilitating the proactive strategy. In the second decision-making phase, DSS users can analyse mitigation measures and select the most suitable to be implemented. The multi-criteria decision model is designed to equivalently use quantitative and qualitative value functions. It is based on a standardized scoring system and aggregates a veto function to prevent the selection of mitigations with an insufficient improvement in efficiency. It considers criteria from the established frameworks, in particular CIA (Confidentiality, Integrity, and Availability), the Common Criteria for Information Technology Security Evaluation according to the ISO/IEC 15408 standard, and the recommended NESCOR criteria for the assessment of the impacts of infrastructure failures. The MITRE ATT&CK, CIS Critical Security Controls, and ACSC frameworks are applied to identify mitigation measures based on cyber incidents and compromised assets. This process utilizes the mappings between CPE identifiers, CVE vulnerabilities, and MITRE ATT&CK techniques and mitigations.